
Common Criteria Protection is an internationally recognized standard for assessing the security requirements of IT products and services. It provides businesses with an effective way to evaluate their systems and ensure they are secure from threats such as data breaches, cyber-attacks, malware, and other vulnerabilities. With Common Criteria Protection in place, businesses can be sure that their data is safe and secure. Additionally, it can help them comply with relevant regulations like GDPR and HIPAA. Ultimately, Common Criteria Protection helps organizations protect their valuable information while simultaneously allowing them to maintain compliance with industry standards.
I. Introduction
II. What is Common Criteria Protection?
III. Advantages of Common Criteria Protection for Businesses
IV. Best Practices for Implementing Common Criteria Protection
V. Conclusion
Protecting data is a major concern for businesses since it can be the target of cybercrime or other malicious activities. Common Criteria Protection (CCP) is an internationally recognized standard that helps ensure security products meet specific criteria and offer assurance that data is properly safeguarded. This blog will explain what CCP is, how it works, some examples of its advantages for businesses, and best practices for implementing it within your organization.
The CC Protection framework was developed by the International Organization for Standardization (ISO) to create a uniform set of standards that vendors could use to evaluate their products and services. In essence, it is an evaluation process in which security products are tested against a set of criteria – established by organizations like the National Institute of Standards and Technology (NIST) or the Information Security Forum (ISF) – to ensure that they meet specific requirements for secure data protection.
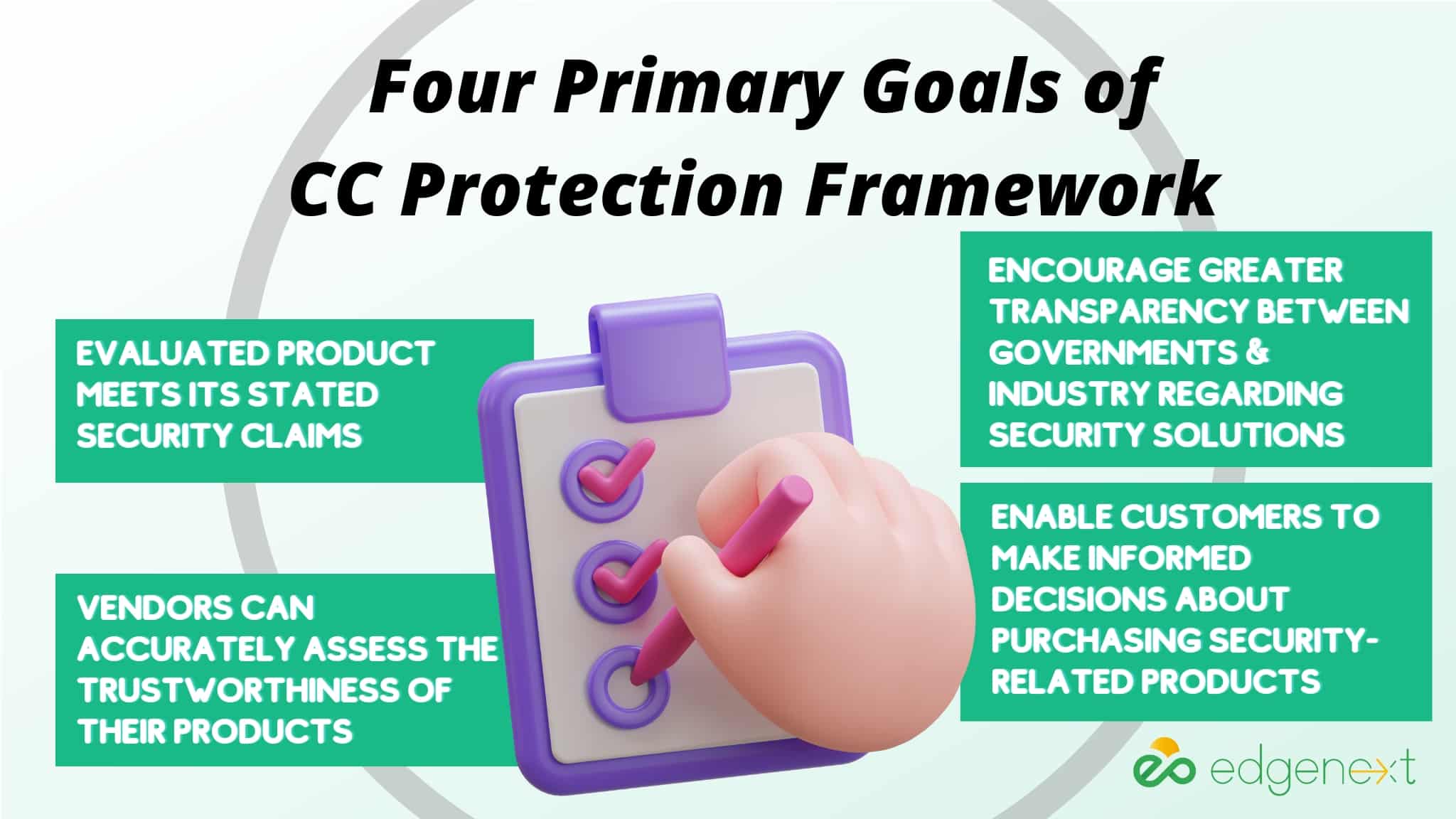
The CC Protection framework was created with four primary goals in mind:
• To assure that the evaluated product meets its stated security claims
• To make sure vendors can accurately assess the trustworthiness of their products
• To enable customers to make informed decisions about purchasing security-related products
• To encourage greater transparency between governments and industry regarding security solutions
The evaluation process begins with a vendor submitting their product for testing against the criteria. The tests involve a hands-on assessment of the product’s security features and a review of the vendor’s documentation and code. Once approved by an accredited third-party certification body, the product is considered Common Criteria certified and can be used by customers to meet specific regulatory requirements or standards.
How Does It Differ from Other Security Standards?
One of the primary benefits of CCP is that it offers vendors a unified set of criteria they can use to evaluate their products against other similar solutions on the market. This helps provide greater confidence in the trustworthiness and reliability of those products and helps ensure that customers are getting the most secure and reliable solutions available.
Unlike other security standards, CCP does not require vendors to meet specific technical requirements – such as a particular type of encryption or authentication method – for their products to be certified. Instead, it relies on testing products against a set of criteria designed to assess the overall security of the product rather than just its components. This helps ensure that vendors can provide their customers with the best protection without making costly adjustments or changes to their existing security measures.

By implementing CCP as part of their data protection strategy, businesses can benefit from the increased trust in the products and services they use and greater flexibility in designing their security solutions. The framework also provides several other advantages for businesses, such as:
• Enhanced customer confidence and trust in the products they buy
• Improved compliance with industry regulations and standards
• Increased ability to protect data from malicious attacks or unauthorized access
• Reduced risk of legal liability due to data breaches or unauthorized access
• Easier comparison between different products on the market
To get the most out of CCP, businesses should follow certain best practices when implementing it within their organization. Here are some tips for ensuring successful implementation:
• Ensure that a qualified third-party certifier conducts the evaluation process
• Develop a comprehensive data protection strategy that covers all potential risks to your organization’s data
• Clearly articulate the roles and responsibilities of different stakeholders involved in the implementation process
• Regularly evaluate products against CCP criteria to ensure they remain up to date with current security standards and monitor compliance with industry regulations on an ongoing basis.
By following these best practices, businesses can ensure that their data remains secure and protected while helping meet regulatory requirements or standards. They can also take advantage of CCP’s unified framework for evaluating security solutions, allowing them to make better-informed decisions when selecting the right products for their organization.
Common Criteria Protection is an effective way for businesses to ensure that the products and services they use comply with industry regulations while also helping them to protect their data from malicious attacks or unauthorized access. By following best practices when implementing CCP within their organization, businesses can take advantage of its unified framework for evaluating security solutions and making better-informed decisions about which products are most suitable for their specific needs. With this in mind, CCP can be a powerful tool in any business’s data protection strategy.

© 2025 EdgeNext Copyright All Right Reserved