
DDoS attacks remain among organizations’ most prevalent security threats and have become increasingly sophisticated. Distributed Denial of Service (DDoS) attacks are a type of attack that floods computers with an overwhelming number of requests in order to disrupt regular services or operations. DDoS attackers can use various methods to gain access to and overwhelm a target, including volumetric attacks, protocol attacks, application layer attacks, and more. This blog post will discuss the different types of DDoS attacks and how organizations can protect themselves from them.
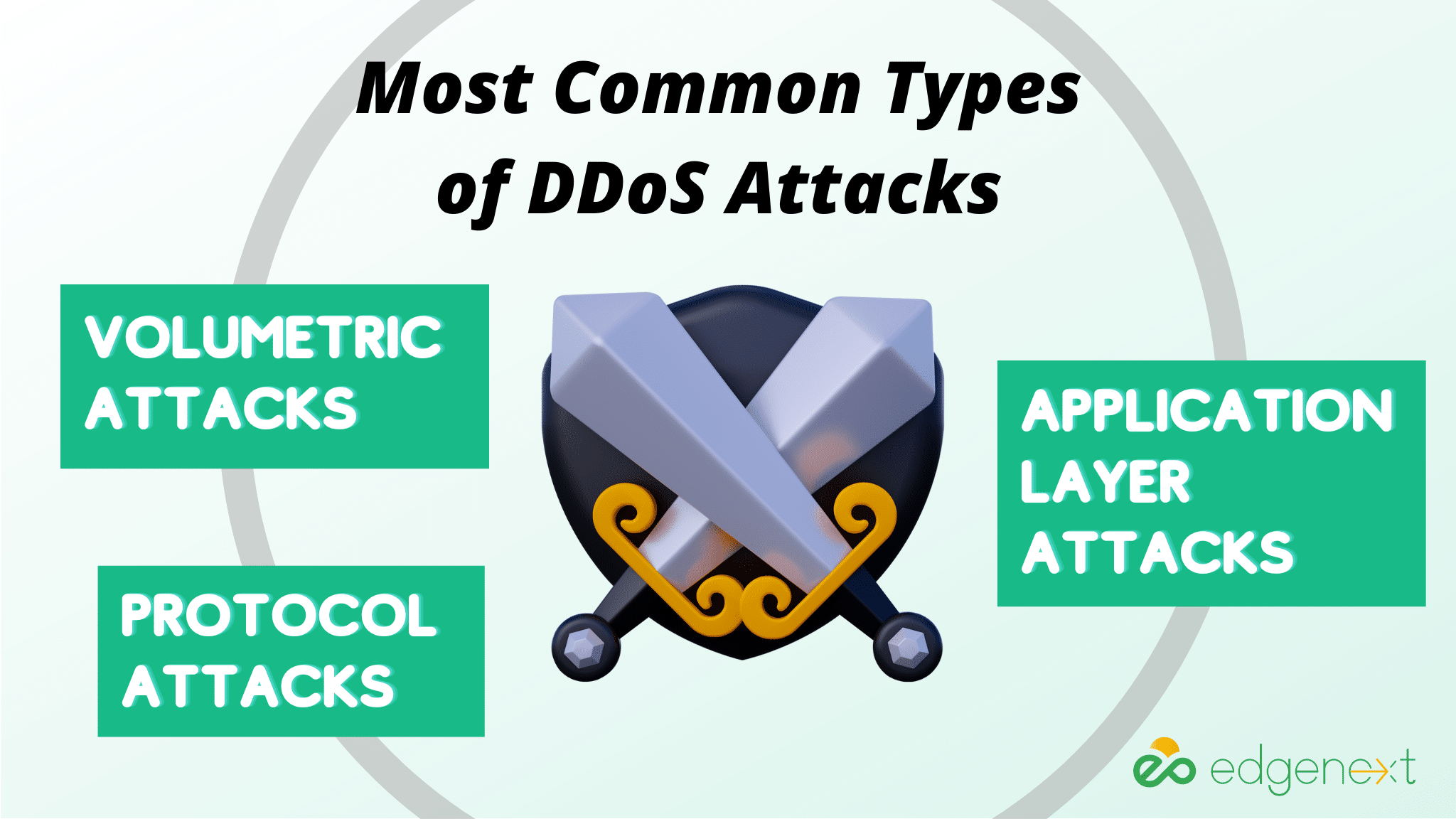
1. Volumetric Attacks
Volumetric attacks involve flooding the target’s network resources with large amounts of data traffic or packets to overwhelm it. The attacker may use multiple computers to increase the bandwidth, the number of requests and the type of requests, making it difficult for legitimate users and services to access the network. Common types of volumetric attacks include UDP floods, ICMP floods, and SYN floods.
2. Protocol Attacks
Protocol attacks exploit weaknesses in underlying networking protocols such as TCP/IP or DNS by sending malformed or malicious packets that cause applications to crash or become unresponsive. These attacks are often used to take down web servers and can be challenging to detect and mitigate. Standard protocol attack methods include teardrop attacks, smurf attacks, ping of death attacks, and more.
3. Application Layer Attacks
Application-layer DDoS attacks target protocols such as HTTP and HTTPS, often by sending large numbers of requests from multiple geographically diverse computers. These attacks are typically used to disrupt web-based applications such as online banking or e-commerce sites. Attackers may also use application layer attacks to bypass network security measures in place to detect volumetric and protocol-based DDoS attacks.
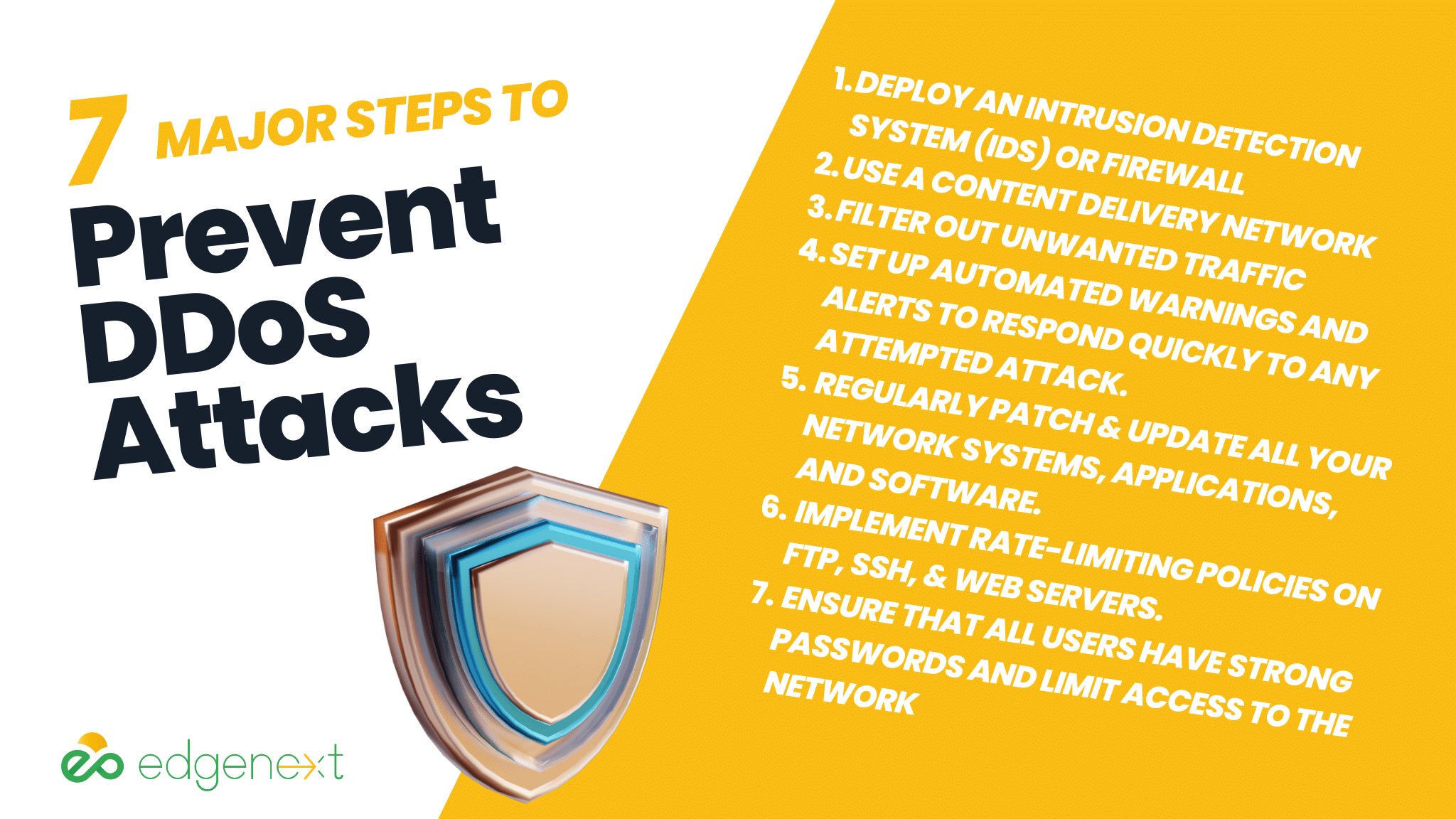
Fortunately, there are several steps organizations can take to protect themselves against DDoS attacks:
• Deploy an intrusion detection system (IDS) or firewall to monitor for malicious activity on the network.
• Use a content delivery network (CDN) like EdgeNext to shield your website from attack traffic while allowing legitimate visitors access.
• Filter out unwanted traffic with a DDoS mitigation service.
• Set up automated warnings and alerts to respond quickly to any attempted attack.
• Regularly patch and update all your network systems, applications, and software.
• Implement rate-limiting policies on vulnerable services like FTP, SSH, and web servers.
• Ensure that all users have strong passwords and limit access to the network by using multi-factor authentication (MFA).
By taking the above steps to protect against DDoS attacks, organizations can significantly reduce their risk of becoming victims of these destructive threats. With the proper measures, businesses can stay one step ahead of attackers and ensure their networks remain secure.
In conclusion, DDoS attacks can cause massive disruption to a network and its services. Organizations need to be aware of the different types of DDoS attacks and how to prevent them. By deploying an IDS or firewall, using a CDN, filtering out unwanted traffic with a DDoS mitigation service, setting up automated warnings and alerts, regularly patching and updating all systems, implementing rate-limiting policies on services such as FTP, SSH, and web servers, and ensuring that users have strong passwords with MFA enabled; organizations can drastically reduce their risk of becoming victims of these malicious threats.
© 2025 EdgeNext Copyright All Right Reserved